Hey there, fellow digital wanderers! Ever wondered how you can keep your precious image files safe from prying eyes? If you’ve ever been curious about securing your pictures with the power of encryption, you’re in the right place. Encryption isn’t just about locking text data in a digital vault—your images can also enjoy the same high level of security. In this article, we’re diving into the world of encryption algorithms for image files, exploring how they work, and discussing the top methods to shield your cherished memories.
Read Now : “preventing Unauthorized Access To Images”
Understanding Image File Encryption
First things first, what exactly is image file encryption? Simply put, it’s the process of converting your image data into a format that is unreadable without a proper decryption key. Imagine it like encoding your images into a secret language only you and select others can comprehend. When you think about encryption algorithms for image files, think about multi-layered security. These algorithms scramble the individual pixel data, cryptographically transforming your JPEGs, PNGs, or any other image format into a secure bundle of digital gibberish that can only be unlocked by those who hold the key.
Encryption algorithms for image files generally work just like they do for text. However, the focus is twisted towards managing pixel values and data integrity, ensuring your images aren’t distorted when decrypted. Among the popular encryption protocols, AES (Advanced Encryption Standard) stands out as one of the top choices. Its robust structure and reliability make it perfect for both professional and personal use, offering a sense of digital confidence. Another notable mention is RSA (Rivest-Shamir-Adleman), commonly used for securing transmission over the internet. Both add their unique touch to the art of securing images, giving you various choices based on your specific needs.
The beauty of encryption algorithms for image files lies in their versatility. Whether you’re safeguarding personal photos or confidential professional images, these algorithms provide a peace of mind that’s hard to quantify in words. You can be sure your images are protected from unauthorized access while maintaining the quality and integrity that made them special in the first place. Embark on this journey to master the encryption of your visual treasure trove, make it Sith-resistant, and rest easy knowing that your data is as safe as a digital fortress.
Benefits of Image File Encryption
1. Data Protection: Encryption algorithms for image files ensure your images are protected from unauthorized access, keeping those unwanted eyes away.
2. Privacy Assurance: Whether it’s personal photos or confidential project images, these algorithms help maintain your privacy by transforming images into an undecipherable format.
3. Integrity Maintenance: Encryption ensures your images remain intact and unaltered during storage or transmission, maintaining their original quality when accessed.
4. Compliance Support: For businesses, encrypted images can help comply with privacy regulations, supporting legal requirements for data protection.
5. Trust Building: Have peace of mind knowing your photos are protected, instilling confidence in personal or business interactions.
How Image Encryption Works
So, how do encryption algorithms for image files differentiate themselves from regular text encryption, you ask? Dive deep with me here as we explore how this trend is taking the internet by storm. In essence, encrypting an image means transforming its pixel data into a coded form. Think of it as turning every picture into a secret puzzle. Whether you’re securing photos of Fido the dog or sensitive images from your latest project, encrypting your images means ensuring they’re safe even if they fall into the wrong hands.
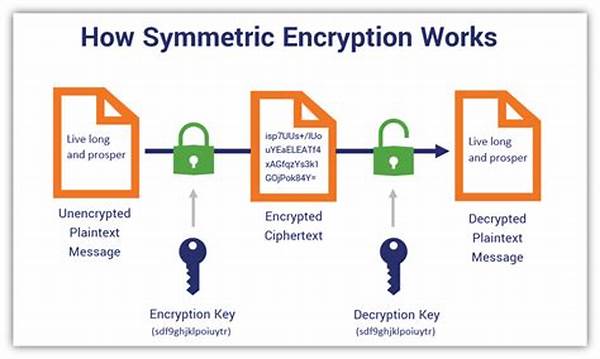
We’ve got a slew of colorful methodologies to explore. For instance, symmetric key encryption uses the same key for both encrypting and decrypting your image files. While it’s often faster, the challenge lies in securely sharing this key. Asymmetric key encryption, on the other hand, plays the role of the smart twin—using a pair of keys where one locks and the other unlocks. Voila! Now you’ve got two options to play with when considering encryption algorithms for image files.
The road doesn’t stop there. Once encrypted, your image files aren’t just protected; they’re shielded from unauthorized tampering and alterations. These encryption algorithms for image files ensure seamless transfer over networks, beaming encrypted data only to be unscrambled by the rightful owner. Let’s just say, your images are practically a vault, and you, my friend, hold the key!
Different Types of Image File Encryption Algorithms
1. AES (Advanced Encryption Standard): Commonly used due to its speed and security, AES encrypts image data effectively.
2. RSA (Rivest-Shamir-Adleman): Popular for encrypting data sent over the internet, it applies a public-key technique.
3. DES (Data Encryption Standard): An older method, often replaced by AES but still used in legacy systems.
4. Blowfish: Known for its speed and effectiveness, Blowfish is a strong contender for encrypting images.
Read Now : Advanced Magnification Technology Lenses
5. Twofish: A successor to Blowfish offering faster encryption and secure data protection.
6. IDEA (International Data Encryption Algorithm): Utilized for secure image transmission and files.
7. Triple DES: A more secure form of DES that applies encryption three times.
8. ECC (Elliptic Curve Cryptography): Offers strong encryption for image files with smaller keys.
9. Serpent: Another AES finalist with strong encryption for image files.
10. RC4: A stream cipher, less common for image encryption but sometimes utilized in specific applications.
Importance of Choosing the Right Algorithm
So, let’s pause and discuss what makes picking the right encryption algorithm for image files crucial. First, not every algorithm will suit every purpose. You might ask why this is so vital—well, let me spill the beans. If you’re encrypting personal photos, speed and ease might be your key points. In those cases, algorithms such as Blowfish or AES may be your go-to solutions because of their balance between speed and security. On the flip side, if you’re dealing with legal documents or sensitive military data, the emphasis on security might lead you to choose RSA or ECC.
Another factor to consider relates to size and complexity. RSA, for instance, can be slower for large data files because of its computational intensity but offers robust security for data-in-transit. AES, on the contrary, gets the job done more swiftly, making it splendid for live streaming image encryption. Ultimately, choosing the right encryption algorithms for image files is all about knowing what best aligns with your goals. This careful selection process ensures you’re covered from all angles, promising your images stay under wraps until you’re ready to unlock them.
It’s also important to consider future scalability and potential regulatory compliance needs. Some industries have specific requirements dictating which encryption protocols must be followed. Without keeping these criteria in mind, you’d risk falling behind in industry standards or even face legal implications. Encryption algorithms for image files do more than just lock your data away—they’re the locksmiths of the 21st century, always adjusting to ensure security measures meet the evolving challenge of the digital age.
Encryption in the Real World
Alrighty, folks, let’s wrap this up with a real-world look at using encryption algorithms for image files. Picture this scenario: You’re a budding photographer capturing stunning moments and selling digital images online. The last thing you want is someone grabbing those images unauthorised and claiming they’re their own, right? With encryption, you’re creating a digital barricade. Only those clients who receive the decryption key can access their purchased images, ensuring your hard work is both safe and recognised.
Even if you’re not in the photography business, encryption plays a considerable role in our daily digital interactions. Social media platforms employ these algorithms to protect user images, while businesses often encrypt images to comply with privacy laws and protect client data. Encryption is no longer just an option; it’s becoming a necessity for safeguarding personal and commercial interests.
In essence, using encryption algorithms for image files gives you an edge over potential breaches. You’re not just protecting data—you’re building a shield of trust around your creations and interactions. Think of it as your digital superhero cape, swaying in the background of everyday connectivity. With this toolkit of knowledge at your fingertips, you’re armed and ready for whatever the digital landscape throws your way!